The world of modern business moves at a very fast pace every single day. Many firms now struggle to keep up with new tech. Specifically, staying ahead means looking toward a smart and flexible leader. Therefore, hiring a Virtual CTO is now a vital step for your firm. This shift offers a clear map for success and a very professional way to work. It is not just a trend for small teams. In fact, it is a smart investment for any brand today. Consequently, a smart choice helps you build a future proof brand name. You will see a clear gain by following this powerful and strategic lead.
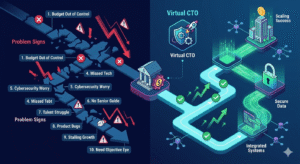
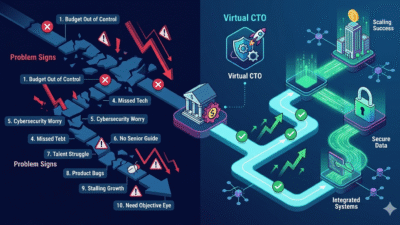
1. Your Tech Budget is Out of Control
Many firms find that their tech costs are far too high. You might spend too much on apps or fixes. First, traditional ways are far too expensive and slow for most small firms. Specifically, poor tech choices can hide many deep and dark costs of old habits. Furthermore, finding a top tool that stays for the long term is rare. You also miss out on fast moves while your output stays low. Similarly, a Virtual CTO helps control your spending. This puts your growth on a steady path for a long time. In contrast, making a strategic tech hire early on helps you save money.
2. You Lack a Clear Tech Roadmap
The journey to the top begins when you pick a dedicated tech path. At this stage, you might wonder why your firm lacks a clear plan. These new tools must act as your top guide on a steady basis. A Virtual CTO ensures your tech and its true worth match your goals. They are built to spark fast progress in every single project. You should also know that an executive partner offers more than a simple task list. While a solo human just finishes a task, a Virtual CTO guides your whole path. Furthermore, they move firms past the fear of bad tech choices early. This approach starts very strong by setting a gold standard for all.
3. Your Team is Stuck in Technical Debt
After you join the model, the goal shifts to gaining big wins. One of the top wins of expert help is getting dedicated guidance. The reality of a modern Virtual CTO then delivers a very custom plan for your firm. This path matches what you need and how you act every day. Therefore, if a project starts, you get fast and clear focus. You also gain access to a very diverse and deep skillset. This includes design, dev, and very deep digital security through smart systems. Access to these skills keeps all your users very happy and safe. It also shows you know your specific needs in a tough market.
4. You’re Missing Out on New Technologies
As a firm’s tech grows, a strategic lead helps you find new ways. At this stage, the focus on a Virtual CTO builds a very strong architecture. This plan is specific to what the modern user likes and wants. For example, some might get a faster way to find new items. The timing of these moves is very key for your success. Furthermore, the leader handles all your vendors and developers with ease. This ensures your project plan is solid from the very first step. Such smart timing helps firms move toward a big global win. Smart leaders push for more scale every single year for you. Indeed, the right partnership reveals who is truly ready.
5. Your Cybersecurity is a Constant Worry
Data is the backbone of all smart marketing and content success today. The way a Virtual CTO works constantly tracks how every user acts with your tech. This includes how they read and share your posts or apps. These facts help refine the paths for every brand you lead. Therefore, the system learns and grows over time to serve you better. This data driven path ensures the best results for your firm. It also prevents any bad risks from hurting your brand name. Smart leadership relies on real facts to win every single time. Your plan and focus are too important to risk at any step. The core of your strategy is about long term brand health.
6. Your Internal Team Lacks Senior Tech Guidance
For the best results, smart tech joins your team in a seamless way. This link ensures all facts stay in one place for your team. Managers and teams share the same live info to move faster. This stops double work and missed ideas for new products or sales. The system provides a full view of every piece you need. Consequently, it supports personal touches at every single step of the way. Your strategy works best when you see a Virtual CTO joined with intelligent tools. It sets a strong base for your future success in any market. Thus, picking the right tech head is about building a real team.
7. You Struggle to Attract Top Tech Talent
Picking the slow path for scaling is a very big risk. You must look for signs that you need a better Virtual CTO for your brand. If your tech is slow, you might need a new plan now. If your costs are too high, experienced systems can fix the leak. The process makes your work much easier and more clear. It also leads to more sales in the long run for you. Businesses that use this path gain a big edge over rivals. Therefore, they work much smarter and not harder to win today. They turn new tech into a tool for more joy and gain. This standard is the path to your best results in life.
8. Your Products Launch Late or With Too Many Bugs
Technical debt can be very hard to handle for a small team. However, the right Virtual CTO makes this work feel very light and fast. First, the system sorts through billions of facts in a second. Specifically, it finds the gold in a mountain of digital noise. Furthermore, this provides you with clear and simple steps to take. You also avoid the stress of being buried in too many bugs. Similarly, the tech presents the info in a way that is easy. This helps your team make fast choices with very high trust. Indeed, the logic of high-level oversight protects your code base. It ensures you do not pay for the same work twice.
9. Your Company Growth is Stalling Due to Tech Issues
The future of your tech is too important to leave to chance. Today, you can gain a top expert view of a Virtual CTO without the huge cost. This smart move helps you scale faster and much smarter too. It turns your tech into a real win for your brand name. You will see more growth and less stress every single day. Therefore, you should act now to secure your spot in the market. Knowing the truth of quality leadership leads to true success. It is the best way to ensure your success for many years. You will find that the right leader makes all the difference. Take this step and watch your business reach new heights soon.
10. You Need an Objective Eye on Your Tech Strategy
The reality is that an outside expert sees things your team might miss. A Virtual CTO offers this fresh, unbiased view. They assess your tech stack, processes, and goals with no internal politics. This objective perspective reveals true bottlenecks and untapped opportunities. Consequently, they help you refine your strategy and make decisions based on solid, impartial advice. Their guidance is crucial for long-term health.
FAQs
1 What is a Virtual CTO?
It is a virtual leader who handles all your tech needs for a lower cost.
2 How does a Virtual CTO help with scaling?
They build a system that can grow without breaking as you get more users.
3 Does it help save money on tech?
Yes, it stops bad debt and makes sure your team works on the right tasks.
4 Is it hard for a small firm to start?
No, it is very easy to scale and it fits firms of any size today.
5 Why is this more than just a simple tool?
It is about a new way to win in a very crowded and fast market.
Read More:
Does your new vcto keep Version 1 from breaking?
How scaling with vCTO gives a better ROI than a freelancer?
Can scaling with a vCTO build a better brand?